The article provides information about DDOS attacks and protection against them.
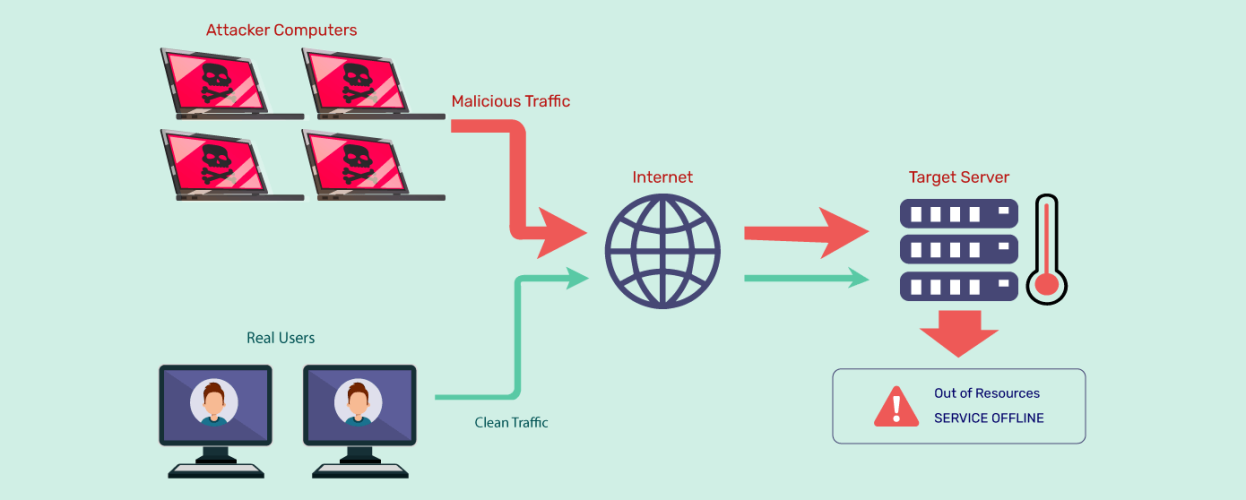
What is a dos attack?
Actually, literally the term “DoS” stands for and is translated as “denial of service”. Accordingly, a dos attack (DOS attack) is an action aimed at provoking such a reaction from the equipment. The term "ddos" translates to "distributed denial of service". Accordingly, a ddos attack (DDoS attack) is a distributed denial of service attack. This type of DDoS attack is carried out from a huge number of different IP addresses belonging to infected computers. What looks like a dos attack is not always what it is. Sometimes a denial of service can be caused by natural reasons - for example, a successful advertising campaign, after which the number of requests to the server exceeds its capacity.
Who needs protection from DDoS attacks?
First of all, a ddos attack is usually aimed at organizations that work with money. Therefore, protection against DDoS attacks is required for online casinos, online stores and banks conducting financial transactions online. During various political events, anti ddos should be used on the websites of parliamentary or presidential candidates. Recent events related to the elections in Ukraine have once again confirmed that protection against DDoS attacks is not a whim, but a necessity. For them, DDoS protection should be even more serious. Moreover, it is better to use hosting with ddos protection.
How to protect a website from ddos?
Protecting a website from DDoS attacks is a relatively new direction in science. More recently, when attacks did occur, they were not very large-scale and could be very easily detected. Now the situation has changed. Experts say that in 2009 the number of attacks increased sharply, so protection against DDoS attacks has become necessary for the successful operation of web resources.
In itself, protection against ddos attacks on a server or website is a process of continuous search for possible threats and their timely elimination. It is best if the protection against ddos attacks is carried out on the operator’s side, since this is where the ddos attack occurs in the first place. As for user computers, protection against ddos attacks on their part will be less effective. The operator should understand that a DDoS attack is inevitable for him anyway, so he needs to be prepared for it. These are the functions that good protection against DDoS attacks performs.
Protection against DDoS attacks in modern conditions
Today, the fight against DDoS has become truly urgent, since as technology develops, not only the skill of specialists who provide decent working conditions on the Internet increases, but also the pressure from hackers increases, who use a wide variety of methods to ensure that a DDoS attack is effective. It is interesting that previously, attackers carried out a completely harmless flood attack on a site, or hackers infected computers with viruses that were quite easy to detect, since as a result of the action of such programs, files disappeared and some programs stopped working. Today, hackers have become more cunning, so a modern DDoS attack is almost invisible to the average user. In addition, attackers are constantly expanding their arsenal of knowledge and skills by developing malicious applications, which make protection against DDoS attacks much more difficult. Unfortunately, modern conditions are such that DDoS protection is one of those issues that requires constant attention.
If you need 100% DDoS protection for your site, then there is a fairly effective way to ensure system security - this is administration. The anti-DDoS method in this case consists of round-the-clock monitoring of possible attacks on the server. In this case, the Ddos attack will be stopped manually.
Reliable protection against DOS attacks is possible in cases of renting a dedicated server. At the same time, protection against DOS attacks lies in the fact that your machine is constantly monitored by data center specialists. If the user is interested in reliable DDoS protection, then with the help of a dedicated server this becomes possible. If the user needs to ensure the safety and security of documents, he can place them on his dedicated server disk space. Protection against DOS attacks will also apply to them.
How to protect against DDoS by clearing traffic
There is another protection against DOS attacks by clearing traffic before it reaches the resource. Today, such protection against DOS attacks is also available and is quite effective, although all disguised and complex attacks require the involvement of operator resources, as well as architecture in order for the attack to be prevented. At the same time, increased anti-ddos protection also includes a variety of software and hardware systems: self-learning systems (ddos protection module), fast detection and instant filtering (ddos protection script). Such protection against DOS attacks will allow the website owner to feel safe.
Sometimes other methods are used to protect a site from DOS attacks, which require deep technical knowledge and skills. In this case, heuristic algorithms are used that are capable of filtering traffic, separating a normal packet from an anomalous one. Such algorithms are constantly updated, because along with new discoveries, the skill of hackers also grows significantly.
Today, the organization of anti-DDoS attack protection can be carried out at various levels and using various tools. All this depends on the company that provides this service. At the same time, the customer and the system operator, as a rule, are in constant contact, and then decide when DDoS protection is necessary and when it can be stopped.
In general, such attacks are now extremely common, so if you know that you have obvious competitors, it is best if you try to protect your resources from possible custom-made attacks. They can be really serious, as a result of which the operation of the system will be paralyzed, and you will lose important clients and, as a result, money.
Well, that’s the end, I wish stability to your hardware!

What is a dos attack?
Actually, literally the term “DoS” stands for and is translated as “denial of service”. Accordingly, a dos attack (DOS attack) is an action aimed at provoking such a reaction from the equipment. The term "ddos" translates to "distributed denial of service". Accordingly, a ddos attack (DDoS attack) is a distributed denial of service attack. This type of DDoS attack is carried out from a huge number of different IP addresses belonging to infected computers. What looks like a dos attack is not always what it is. Sometimes a denial of service can be caused by natural reasons - for example, a successful advertising campaign, after which the number of requests to the server exceeds its capacity.
Who needs protection from DDoS attacks?
First of all, a ddos attack is usually aimed at organizations that work with money. Therefore, protection against DDoS attacks is required for online casinos, online stores and banks conducting financial transactions online. During various political events, anti ddos should be used on the websites of parliamentary or presidential candidates. Recent events related to the elections in Ukraine have once again confirmed that protection against DDoS attacks is not a whim, but a necessity. For them, DDoS protection should be even more serious. Moreover, it is better to use hosting with ddos protection.
How to protect a website from ddos?
Protecting a website from DDoS attacks is a relatively new direction in science. More recently, when attacks did occur, they were not very large-scale and could be very easily detected. Now the situation has changed. Experts say that in 2009 the number of attacks increased sharply, so protection against DDoS attacks has become necessary for the successful operation of web resources.
In itself, protection against ddos attacks on a server or website is a process of continuous search for possible threats and their timely elimination. It is best if the protection against ddos attacks is carried out on the operator’s side, since this is where the ddos attack occurs in the first place. As for user computers, protection against ddos attacks on their part will be less effective. The operator should understand that a DDoS attack is inevitable for him anyway, so he needs to be prepared for it. These are the functions that good protection against DDoS attacks performs.
Protection against DDoS attacks in modern conditions
Today, the fight against DDoS has become truly urgent, since as technology develops, not only the skill of specialists who provide decent working conditions on the Internet increases, but also the pressure from hackers increases, who use a wide variety of methods to ensure that a DDoS attack is effective. It is interesting that previously, attackers carried out a completely harmless flood attack on a site, or hackers infected computers with viruses that were quite easy to detect, since as a result of the action of such programs, files disappeared and some programs stopped working. Today, hackers have become more cunning, so a modern DDoS attack is almost invisible to the average user. In addition, attackers are constantly expanding their arsenal of knowledge and skills by developing malicious applications, which make protection against DDoS attacks much more difficult. Unfortunately, modern conditions are such that DDoS protection is one of those issues that requires constant attention.
If you need 100% DDoS protection for your site, then there is a fairly effective way to ensure system security - this is administration. The anti-DDoS method in this case consists of round-the-clock monitoring of possible attacks on the server. In this case, the Ddos attack will be stopped manually.
Reliable protection against DOS attacks is possible in cases of renting a dedicated server. At the same time, protection against DOS attacks lies in the fact that your machine is constantly monitored by data center specialists. If the user is interested in reliable DDoS protection, then with the help of a dedicated server this becomes possible. If the user needs to ensure the safety and security of documents, he can place them on his dedicated server disk space. Protection against DOS attacks will also apply to them.
How to protect against DDoS by clearing traffic
There is another protection against DOS attacks by clearing traffic before it reaches the resource. Today, such protection against DOS attacks is also available and is quite effective, although all disguised and complex attacks require the involvement of operator resources, as well as architecture in order for the attack to be prevented. At the same time, increased anti-ddos protection also includes a variety of software and hardware systems: self-learning systems (ddos protection module), fast detection and instant filtering (ddos protection script). Such protection against DOS attacks will allow the website owner to feel safe.
Sometimes other methods are used to protect a site from DOS attacks, which require deep technical knowledge and skills. In this case, heuristic algorithms are used that are capable of filtering traffic, separating a normal packet from an anomalous one. Such algorithms are constantly updated, because along with new discoveries, the skill of hackers also grows significantly.
Today, the organization of anti-DDoS attack protection can be carried out at various levels and using various tools. All this depends on the company that provides this service. At the same time, the customer and the system operator, as a rule, are in constant contact, and then decide when DDoS protection is necessary and when it can be stopped.
In general, such attacks are now extremely common, so if you know that you have obvious competitors, it is best if you try to protect your resources from possible custom-made attacks. They can be really serious, as a result of which the operation of the system will be paralyzed, and you will lose important clients and, as a result, money.
Well, that’s the end, I wish stability to your hardware!
